We investigate mhyprot2sys a vulnerable anti-cheat driver for the popular role-playing game Genshin Impact. Mobile device and OS.

Which Type Of Device Is The Top Target Of Ransomware Tools Pond
Type of Attack Number of attacks in 2020 Number of attacks in 2021 Growth Spam phishing.
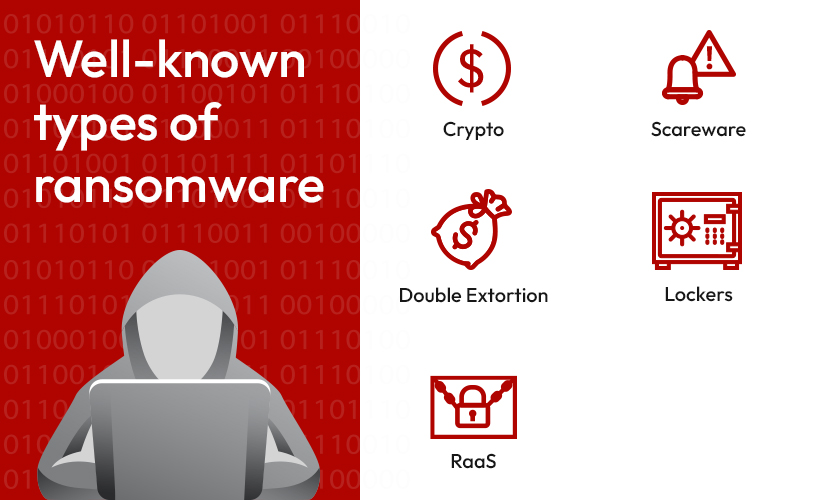
. Ransomware is a growing type of malware hack in which the attacker holds the victim and their personal data for ransom until they comply with ransom demands. The Hkgt ransomware is a kind of malware that encrypted your files and then forces you to pay to restore them. Ransomware is malicious code that renders the files andor operating environment of an endpoint unavailablebe it an end user device or a serveruntil a payment is made to the cybercriminal.
Human-operated ransomware attacks. Ransomware is one of the most common cyber-attacks hitting thousands of businesses every year. Human-operated ransomware is the result of an active attack by cybercriminals that infiltrate an organizations on-premises or cloud IT infrastructure elevate their privileges and deploy ransomware to critical data.
They can include malicious links that download ransomware onto the users device. The authors of ransomware instill fear and panic into their victims causing them to click on a link or pay a ransom and users systems can become infected with additional malware. The driver is currently being abused by a ransomware actor to kill antivirus processes and services for mass-deploying ransomware.
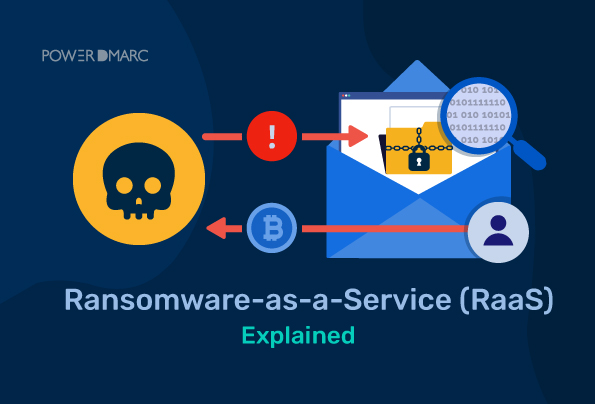
Hive is built for distribution in a Ransomware-as-a-service model that enables affiliates to utilize it as desired. First observed in June 2021 Hive is an affiliate-based ransomware variant used by cybercriminals to conduct ransomware attacks against healthcare facilities nonprofits retailers energy providers and other sectors worldwide. Rank Company TEU 2017.
23 These attacks target the weakest. Determine the ransomware type to enable more targeted remediation efforts. Once downloaded to the users device the malware holds corporate data hostage locking users out or rendering it indecipherable through encryption until the organization pays a ransom to restore it.
Censys assesses that initially discovered Russian Hosts A B with Metasploit and Deimos C2 are possibly initial attack vectors to take over victim hosts. Russian Hosts F G possess malware capable of disabling anti-virus and performing a ransomware attack with beacons to two Bitcoin nodes that likely receive ransomware payment from victims. Ping packets larger than 65535 bytes violate the Internet protocol so the attacker sends them in pieces.
Ransomware displays intimidating messages similar to those below. Efvc Bbii BbyyThis virus encrypt all common file types and adds its. These hands-on-keyboard attacks target an organization rather than a single device.
Mobile ransomware is often delivered via malicious apps and requires that you boot the phone up in safe mode and delete the infected app in order to. Top Cyber Security Statistics Facts Trends in 2022. Click here to resolve the issue.
These attacks have only become more common as they are one of the most lucrative forms of attacks. Here are the top 20 companies by export volume 20-foot equivalent units or TEUs. Ransomware Actor Abuses Genshin Impact Anti-Cheat Driver to Kill Antivirus.
Check out our list of the top 10 cybersecurity threats in 2022. Remove the ransomware which can involve checking if it is deleted using antimalware or anti-ransomware software to quarantine it asking external security professionals for help and if need be removing it manually. Surface Pro X comes in a range of configurations that start with a respectable 900 entry-level device Wi-Fi only and top out at 1800 for a model with 16 GB of RAM LTE support an SQ2.
Isolate the infected device. Once the malware has been installed the hacker controls and freezes you out of it until you pay a ransom. Mobile ransomware typically displays a message that the device has been locked due to some type of illegal activity.
According to Ciscos 2021 Cyber Security Threat Trends report. Once the package is reassembled it disrupts the system overflowing the memory. Just in the past year Zerto have seen ransomware target large and small.
BYOD bring your own device is the increasing trend toward employee-owned devices within a business. Ransomware involves encrypting company data so that it cannot be used or accessed and then forcing the company to pay a ransom to unlock the data. Ransomware is a type of malware.
Cybercriminals use ransomware to take over devices or systems to extort money. Thursday August 25 2022. Note that DjvuSTOP ransomware family was first revealed and discovered by virus analyst Michael Gillespie.
The message states that the phone will be unlocked after a fee is paid. The essential resource for cybersecurity professionals delivering in-depth unbiased news analysis and perspective to keep the community informed. Ping of death is a type of DoS attack in which an attacker sends oversized packets that the targets system cannot handle crashing targeted computers.
Your computer has been infected with a virus. Hkgt virus is basically similar to other representatives of DJVU ransomware like. Smartphones are the most common example but employees also take their own tablets laptops and USB drives into the workplace.
Ransomware is a type of cyberattack involving malware.

Businesses Are Premium Ransomware Targets As Attacks Spike In Last Year

5 Tools That Ll Help Keep Ransomware Off Your Devices Learning Styles Malware Removal Cyber Attack
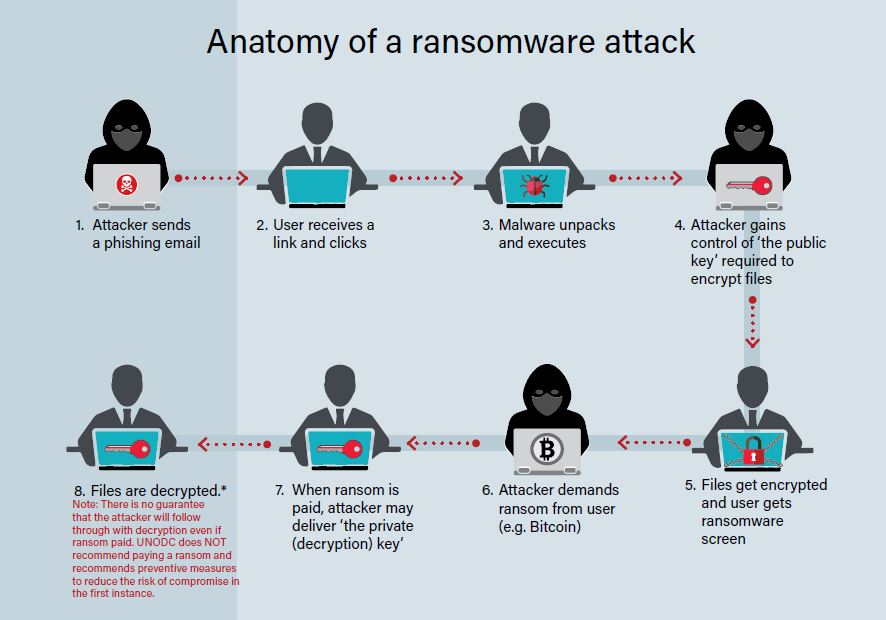
Ransomware Attacks A Growing Threat That Needs To Be Countered

How To Detect And Prevent Ransomware Attacks

Microsoft Warns Against Common Human Operated Ransomware Techniques

How Muninn Detects Lockbit 2 0 Ransomware Attacks

0 comments
Post a Comment